Today I am going to publicly disclose a vulnerability that I have found at Instabug company.
I was able to swap my own normal registered unpaid account with the demo’s highly paid account removing the restrictions on the demo’s account to be placed on my own free account so that gaining full features of the highest plan cost(349$/month) without payment in addition to manipulating normal users to access my account when they are trying to access the demo one.
Started when a great company(Instabug) which tests bugs found in android and IOS apps opened positions for hire.
As a job seeker, I was interested to apply as a penetration tester until I found they are launching a bug bounty program.
After thinking for a while the question was “Could I find a bug at the company that works on hunting application bugs?”
The challenge started
By creating an account I started to test their backend for any unusual actions focusing on XSS vulnerabilities after I recognized that their main website is connected to a secured API that is connected to the database and manages all the user interactions and processes.
After hours of no result, I was about to quit before I noticed that Instabug has a demo account to test their services so “mmmmm let’s try”
The demo logged in automatically after pressing the button “demo account” and as I have noted their entire web application is connected to an API so I fired up the burp suite to intercept the demo request and see what happens behind the scenes. and guess what!!
Yes, it is, the demo account email and password sent to the API in addition to the user’s session token so that any user could login automatically to the demo account.
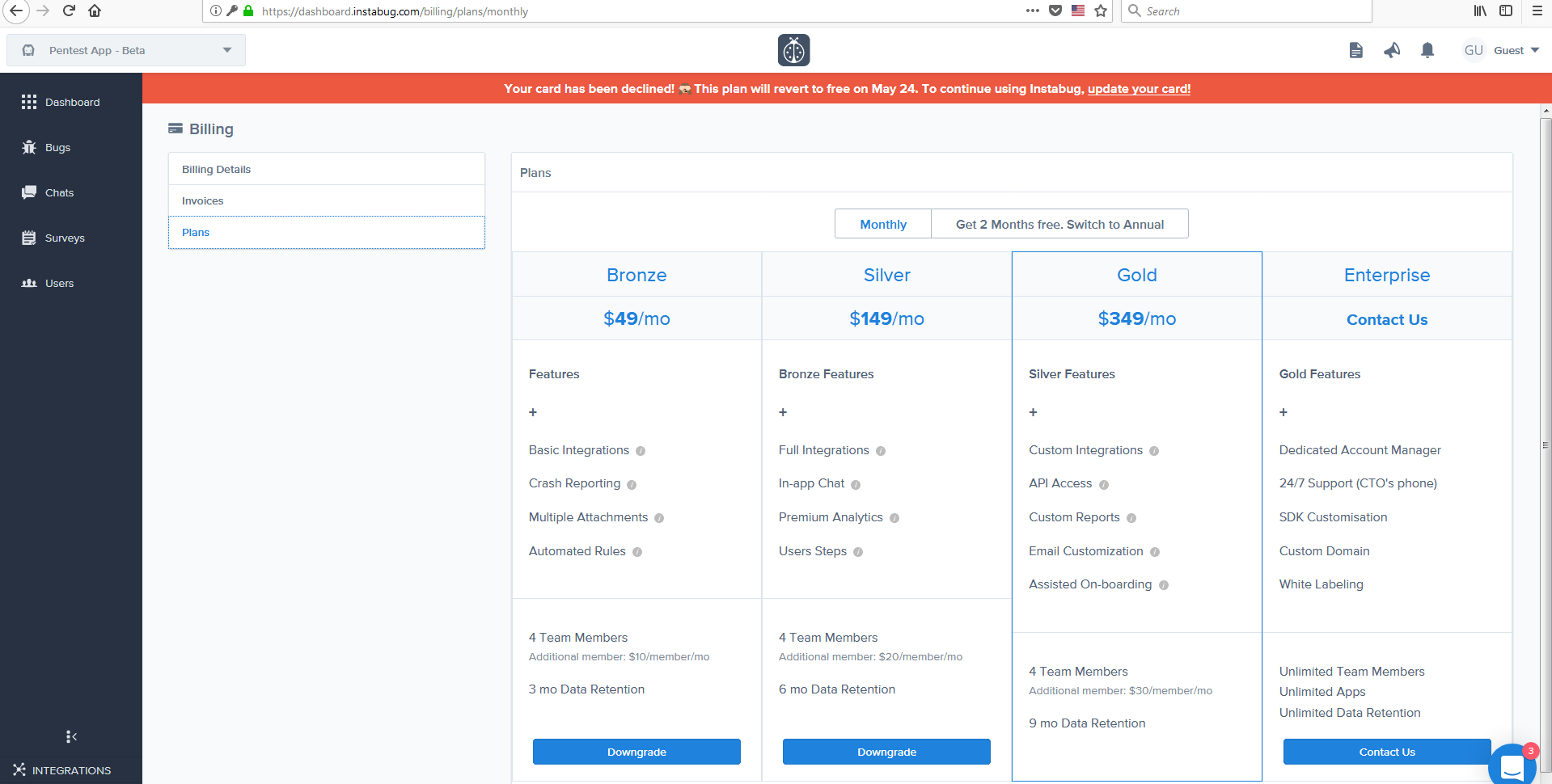
Going in deeper to the demo account I found good news and bad news, the good is that Instabug demo account is attached to the highest plan which is the Gold Plan so that users could test all the services while the bad is that it’s a restricted account as adding, editing or deleting is forbidden or in another format “read-only mode” which means changing the password using the password we have just gathered or any other info is forbidden.
At this point I started to think outside the box if I transferred the demo account from the restricted area then I could have full access to the Instabug gold plan features.
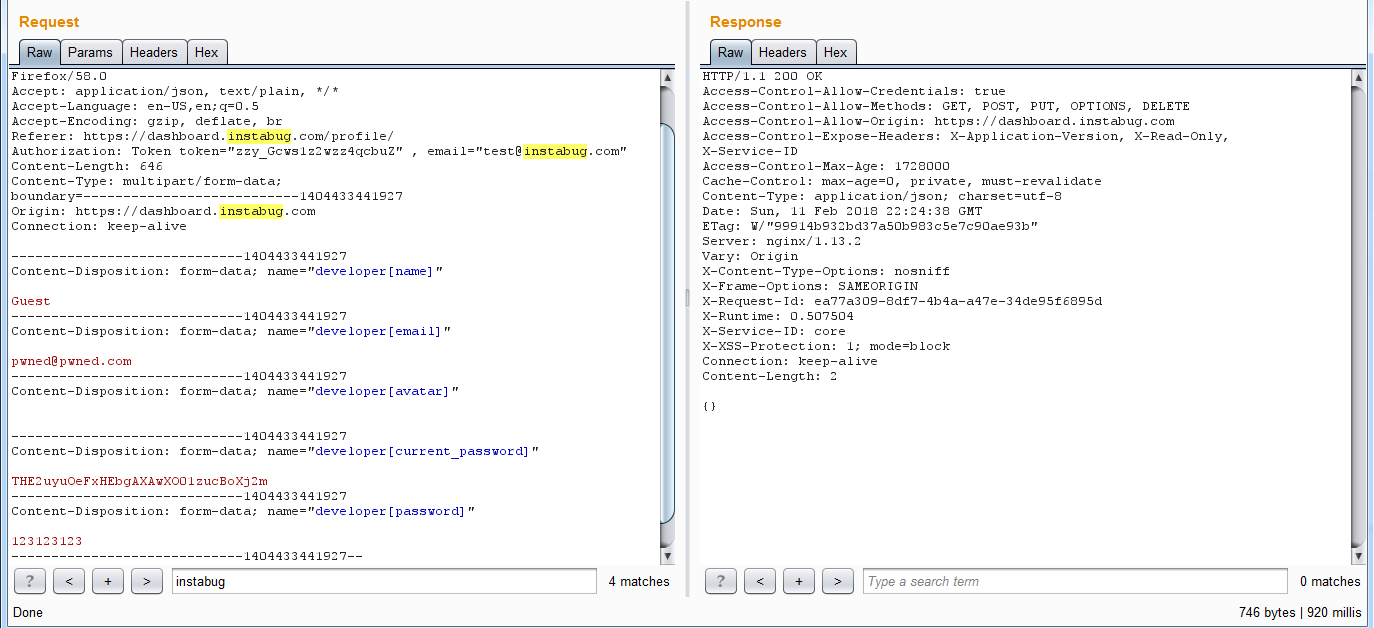
By signing out and signing to my registered account which is unrestricted but without any paid plan, I changed the password and intercepted the API request:

Demo accounts prevent users from changing its password or making any actions but what if I manually sent the request to the API without using the UI.
After logging back into the demo account I edited the burp request by editing the header email and adding the new token to the Authorization HTTP header, I also changed the field value of the current password to the password of the demo account we captured before in addition to changing the email to “pwned@pwned.com” and manually launching the following request.
As shown in the image the API responded with 200 OK which means the request is authorized, accepted, and contains no error. are you sure Mr. API?? 🙂
At this point, I was still not sure the password was changed so the next step was to test the new credentials to confirm that Mr. API is manipulated successfully.
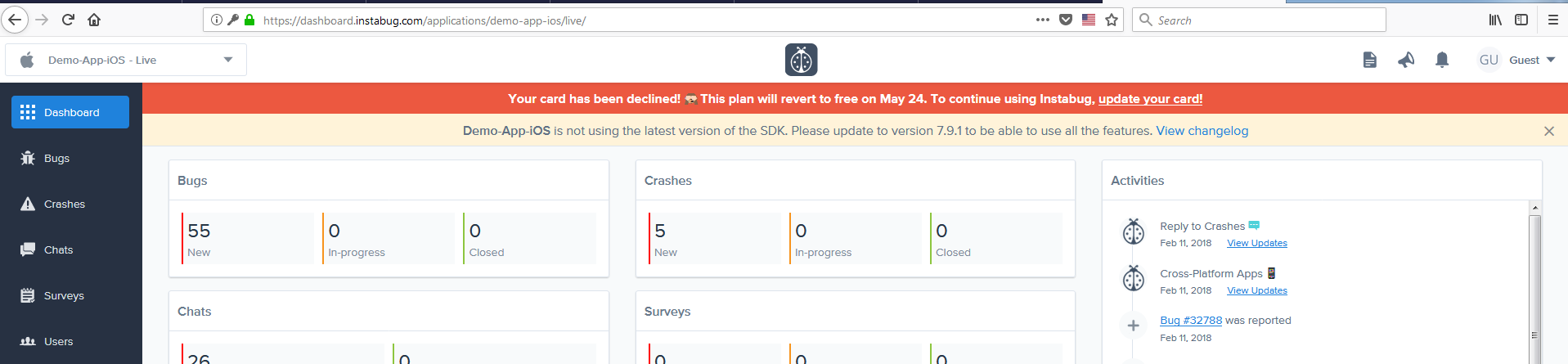
First, I tried the demo’s account normal access by clicking the demo button:
OK now users could not access to the demo account because it was hijacked and it’s email and password forcefully changed see next image:
Yes, I am in and finally, the account is not in the restricted area anymore after it’s mail is changed to have full control on the account with the ability to add, edit, delete and have full access to account management.
Still the most important question to be answered: “Am I still at the Gold Plan?”
After I successfully had the full access to the gold plan I got an idea->
I tried to create a normal registered user account and change its email and password to the default demo account credentials showed at the first image so that if a normal user pressed on the demo button they will be redirected to another normal registered account of mine that contains no plan while the attack was successfully exploited leading to users manipulation.
12 February -> I contacted Instabug company with a detailed report.
15 February -> They replied fast to the report announced the vulnerability exists.
15 February -> The vulnerability is patched and I thankfully have been rewarded at their bug bounty program in HackerOne.
Until next time.