Today I am going to disclose the write-up of one of the most interesting challenges I have been playing recently together with my teammates in the EGCTF 2019.
The challenge was amazing and really challenging, it was only solved twice by our team and another team and today I add the full write up.
OK, let’s start.
Reconnaissance Phase
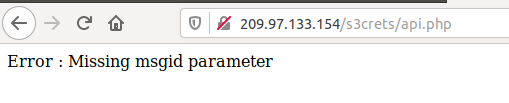
Once I launched the challenge, I see the following:

I tried to launch many bypass authentication payloads like ‘ or 1=1– and similar payloads but all my attempts failed.
Launching verb tampering attacks to bypass the firewall also resulted in a dead-end, at that point I decided to extend my recon phase, so I launched Dirbuster to search if there are more hidden endpoints and I clearly noticed a newly discovered endpoint.
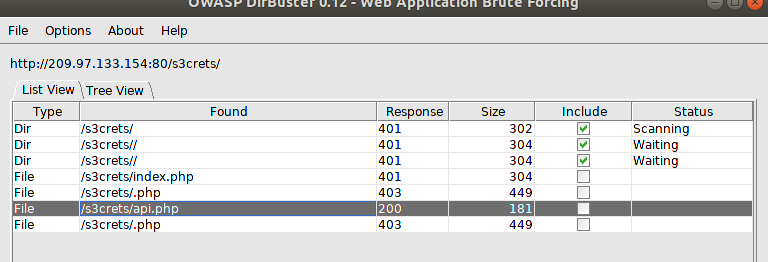
Assessment phase
Now a new hidden endpoint is discovered which is “api.php”, by opening the page we can observe the following.